lab5-2 Wireshark_ICMP
Lab5-2 ICMP
1 Introduction
在这个实验中,我们将探索ICMP协议。
2 Steps
Step 1: ICMP and Ping
让我们从捕获Ping程序生成的数据包开始。首先使用Wireshark开始抓包(使用icmp过滤器),然后在命令行中输入”ping -n 10 www.ust.hk”,待ping程序运行结束后停止抓包。
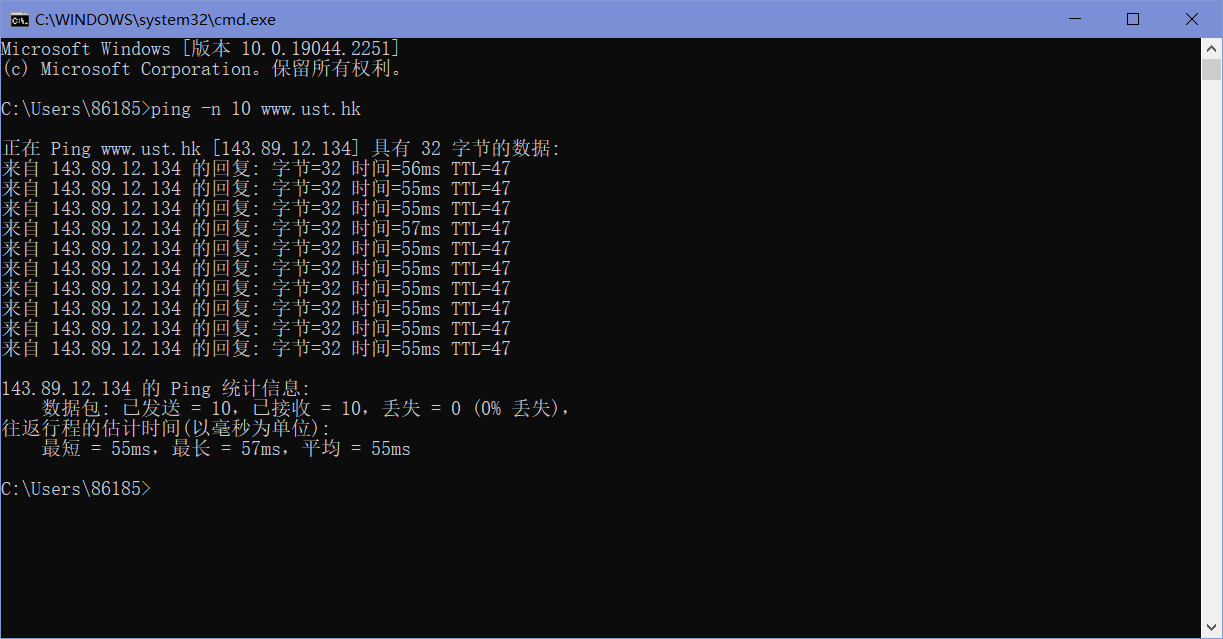
得到如下结果:
1. What is the IP address of your host? What is the IP address of the destination host?
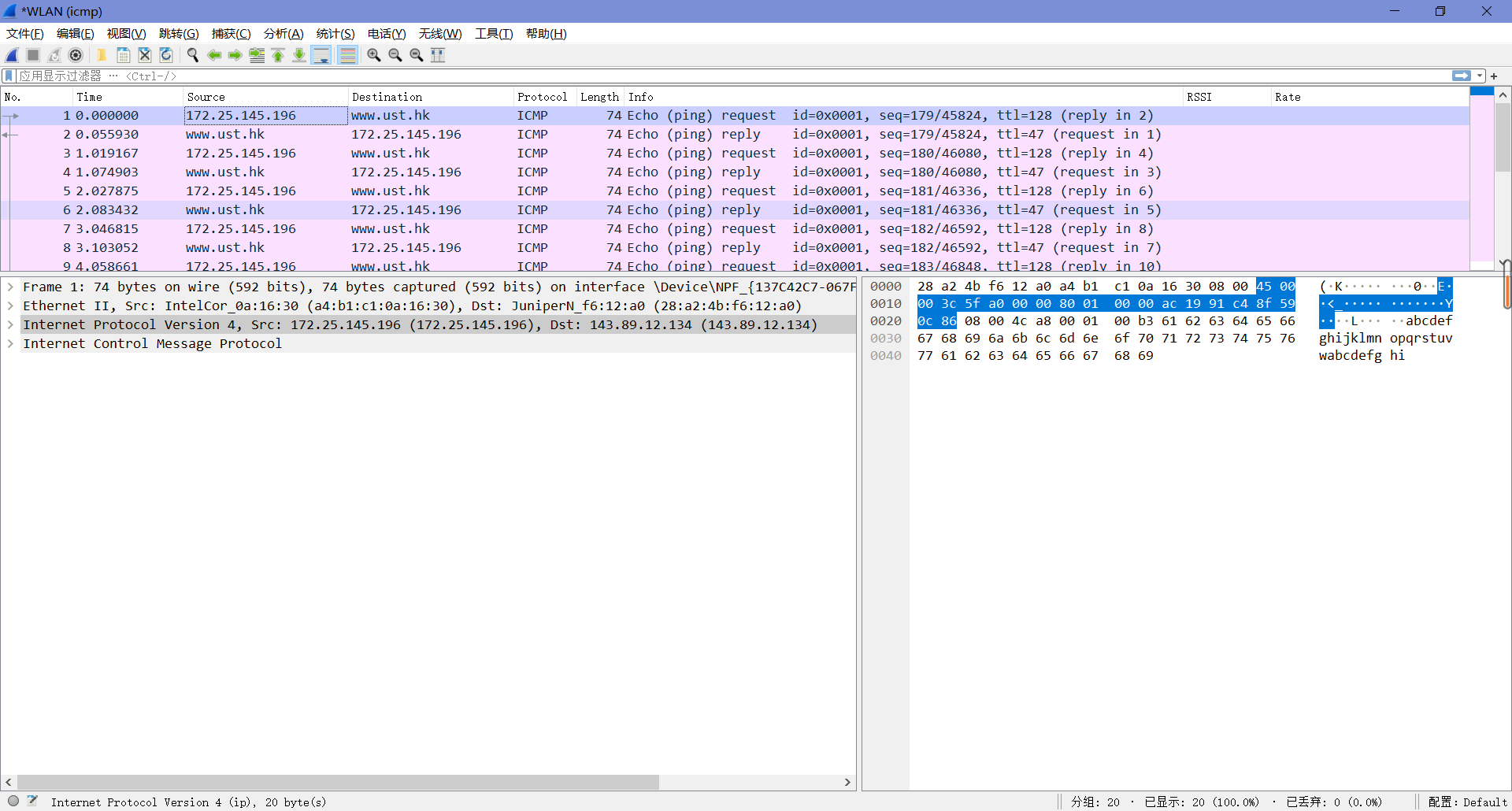
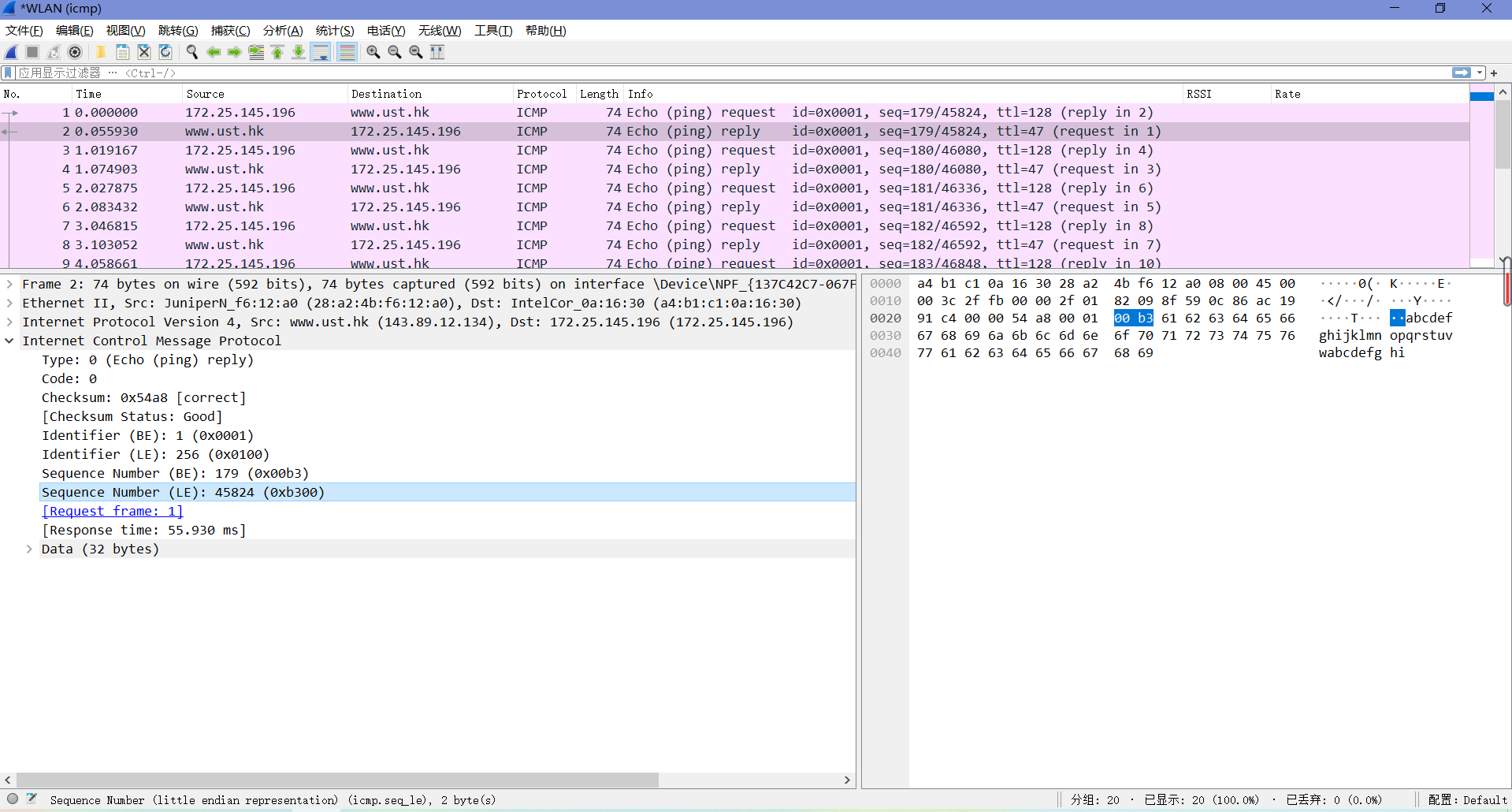
由下图可知,本机IP为172.25.145.196,目标主机IP为143.89.12.134。
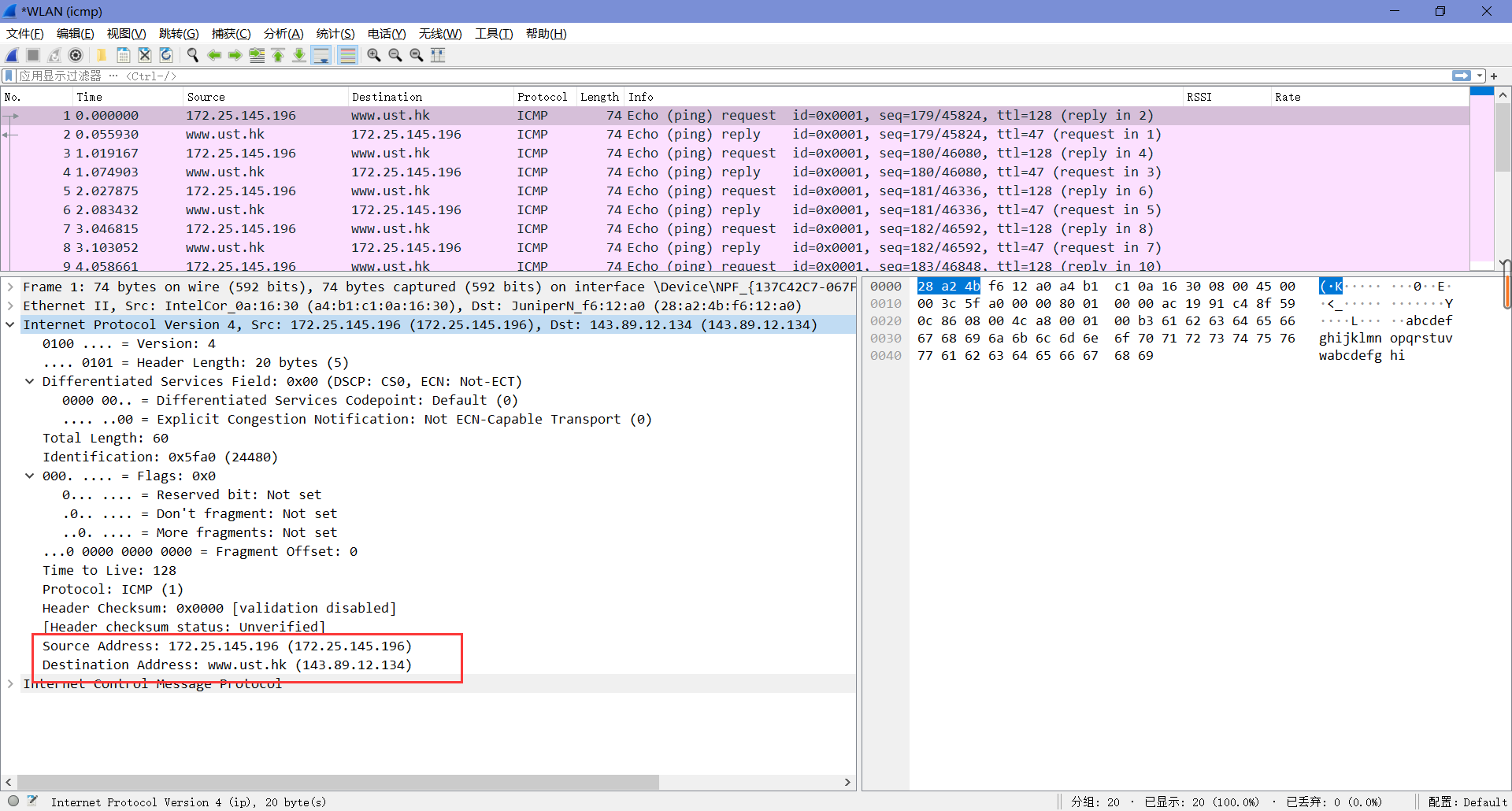
2. Why is it that an ICMP packet does not have source and destination port numbers?
因为ICMP是网络层的协议,它不需要传输层TCP或者UDP的承载,直接使用IP数据报承载,因此不需要源端口号和目的端口号,只要源地址和目的地址即可。
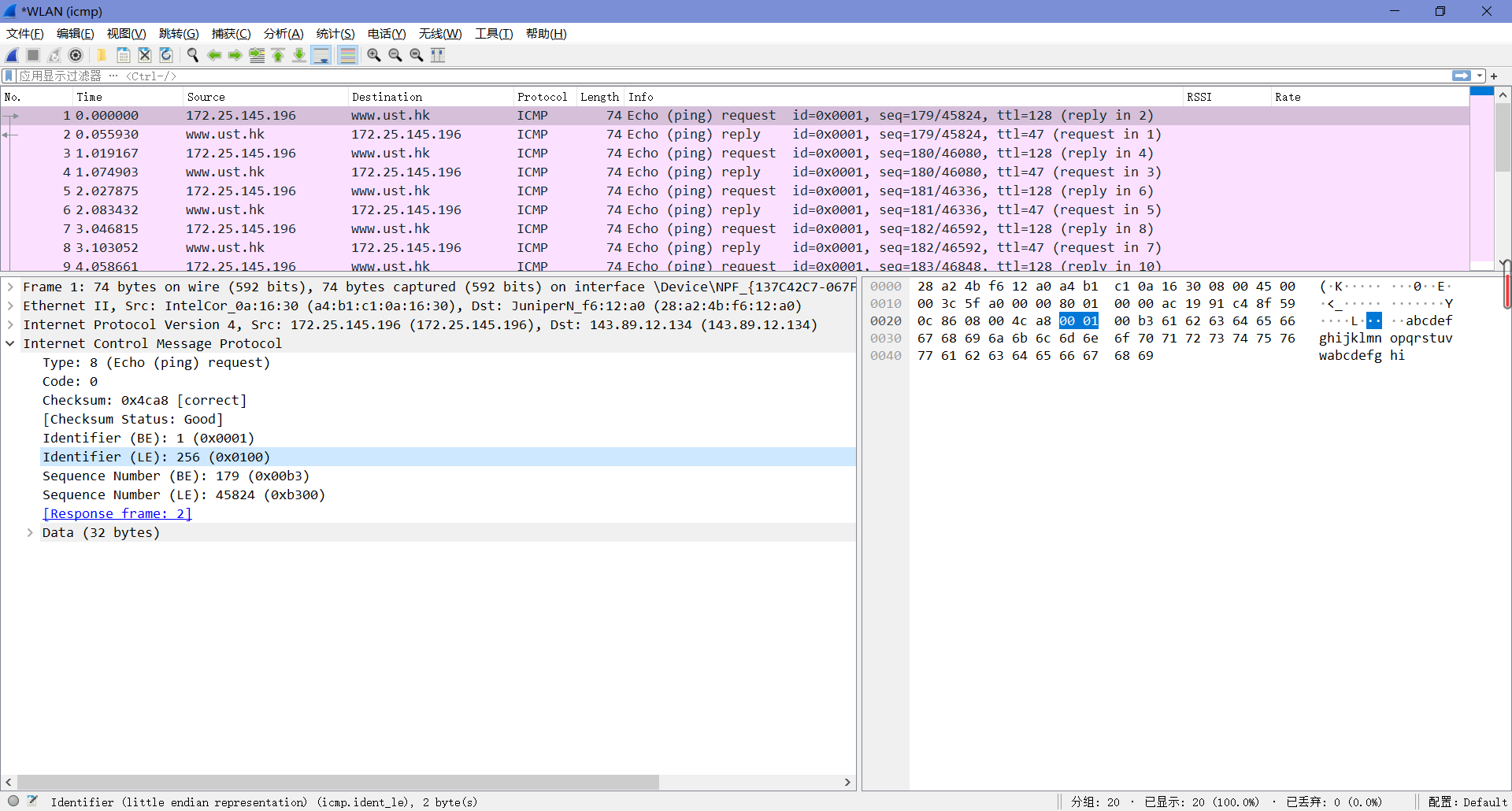
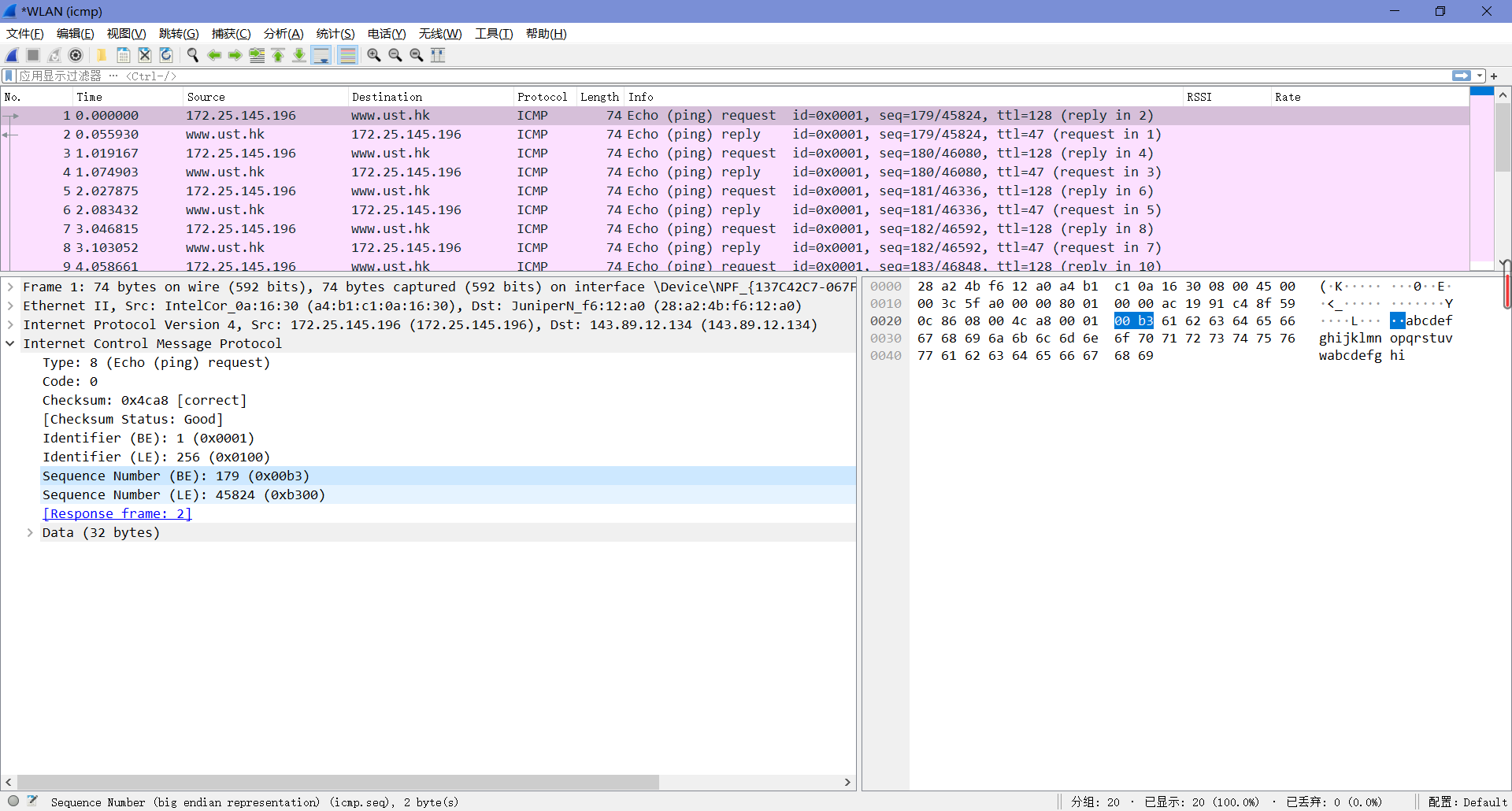
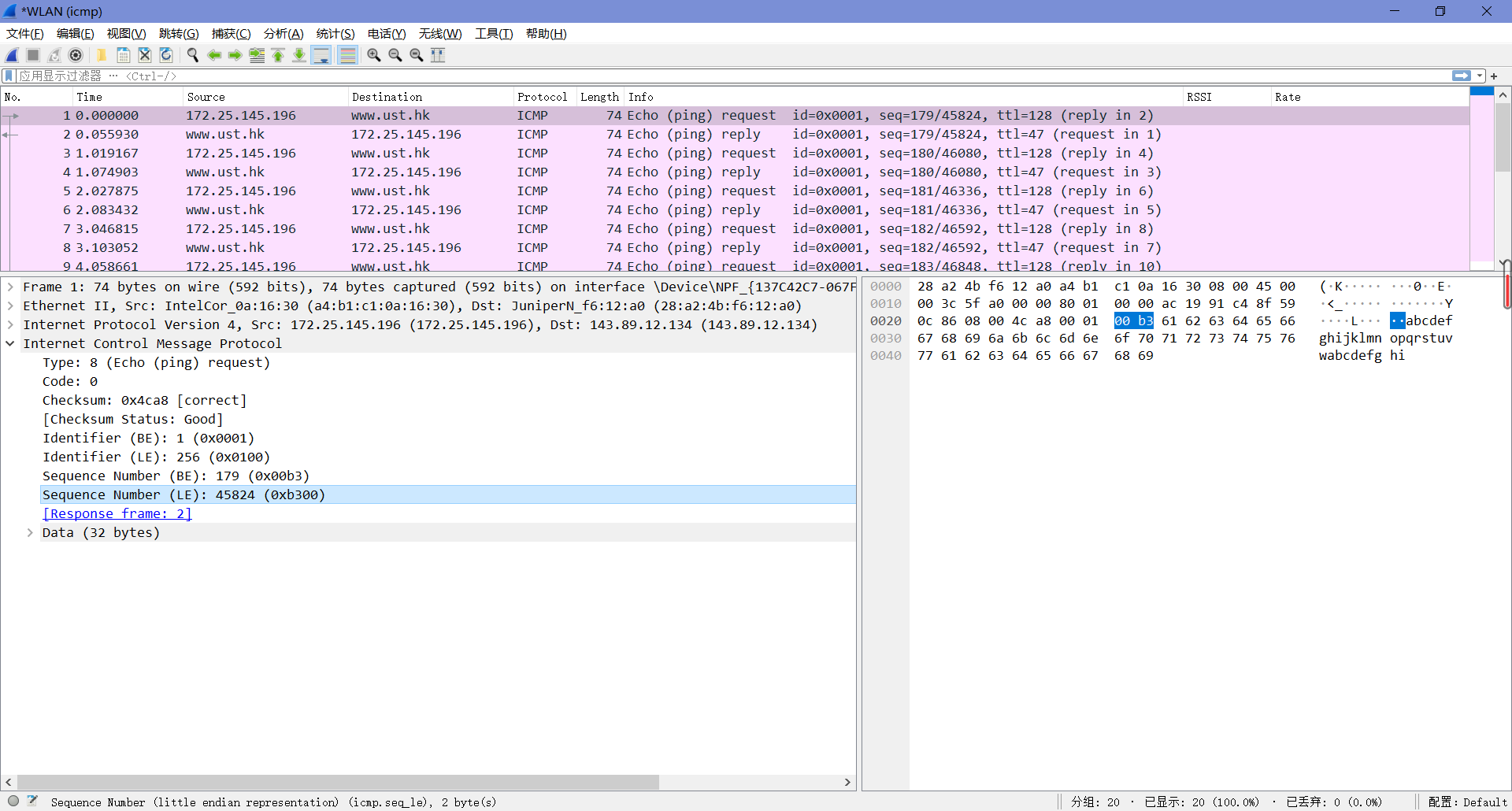
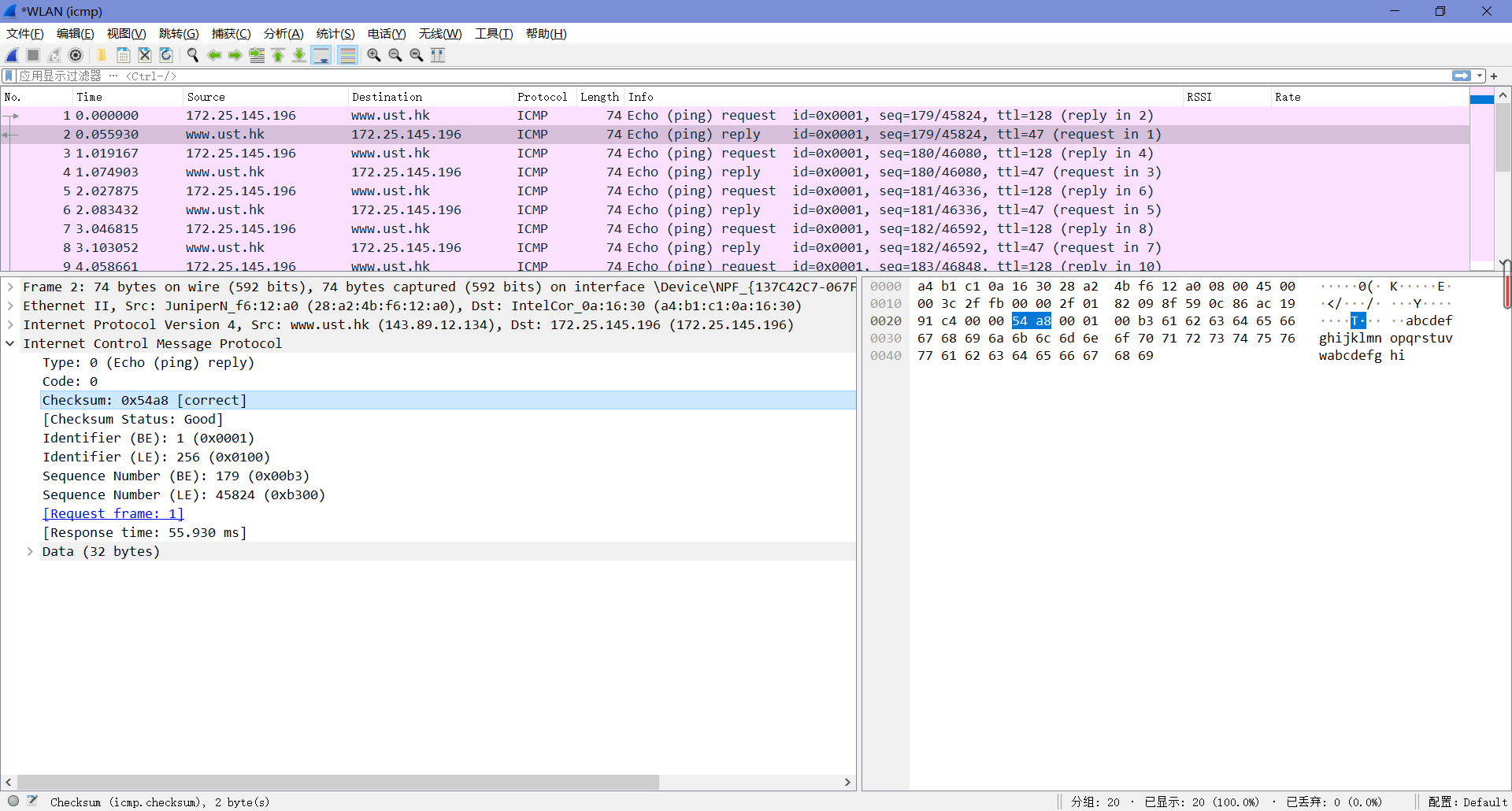
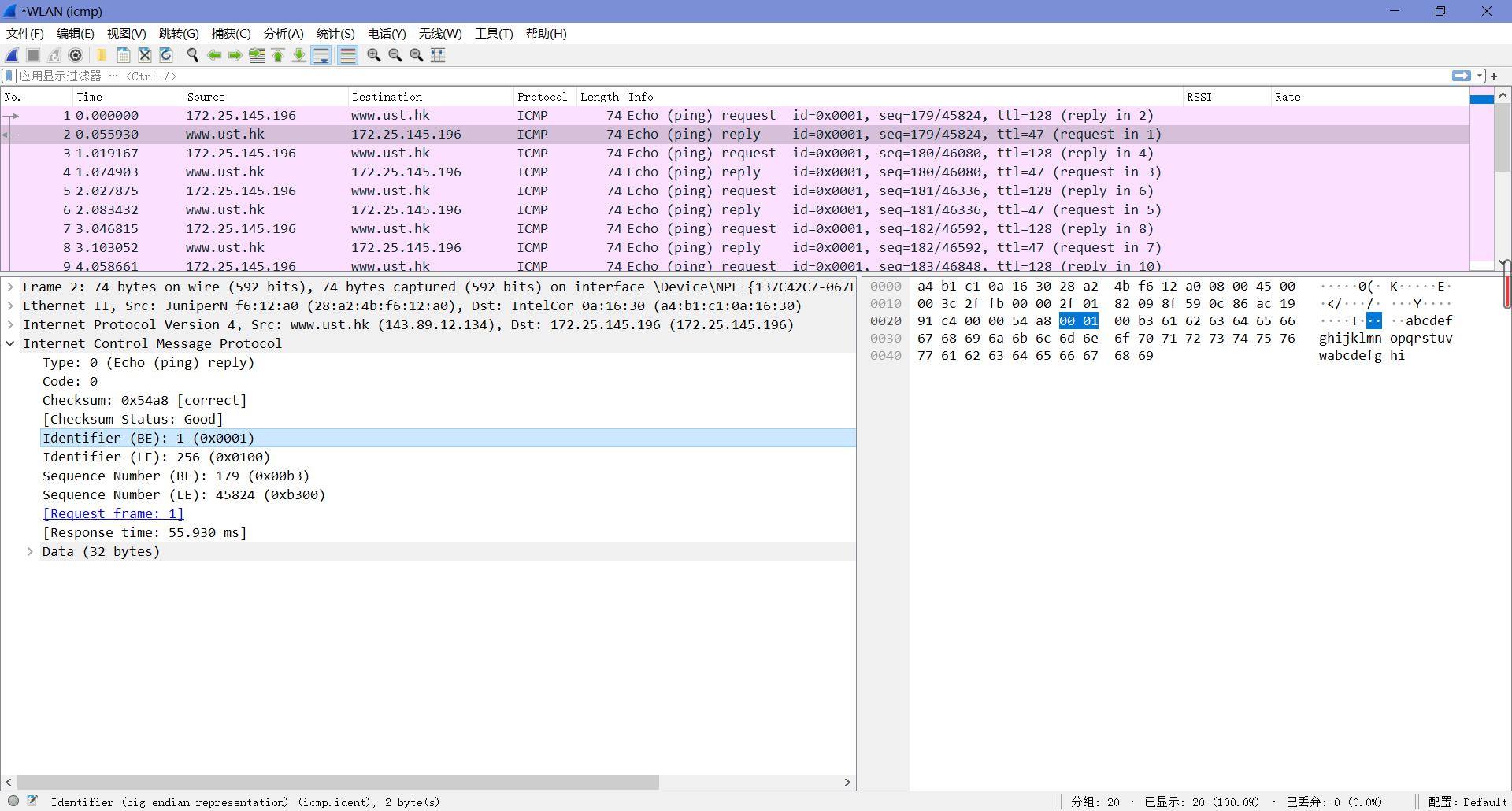
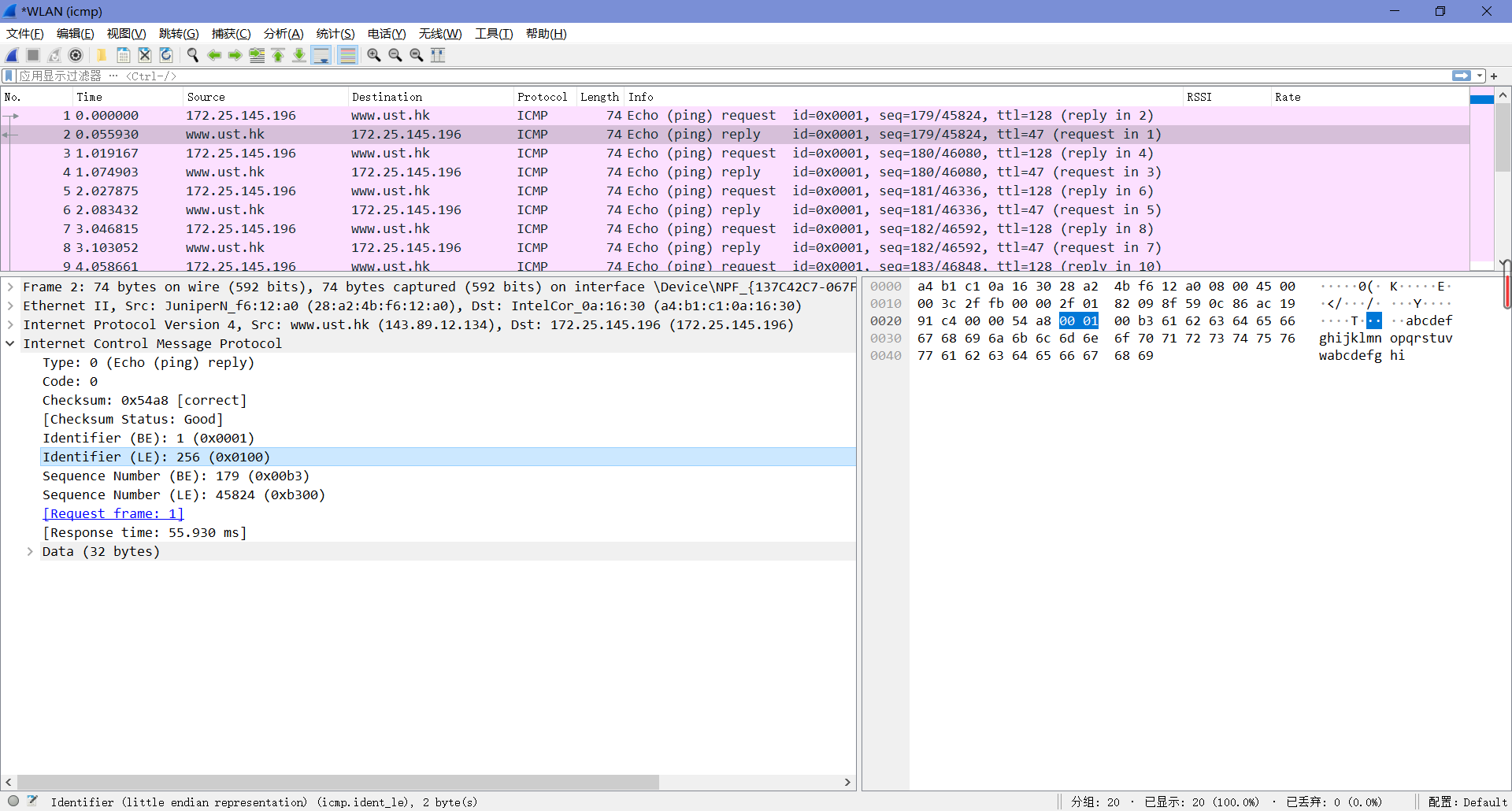
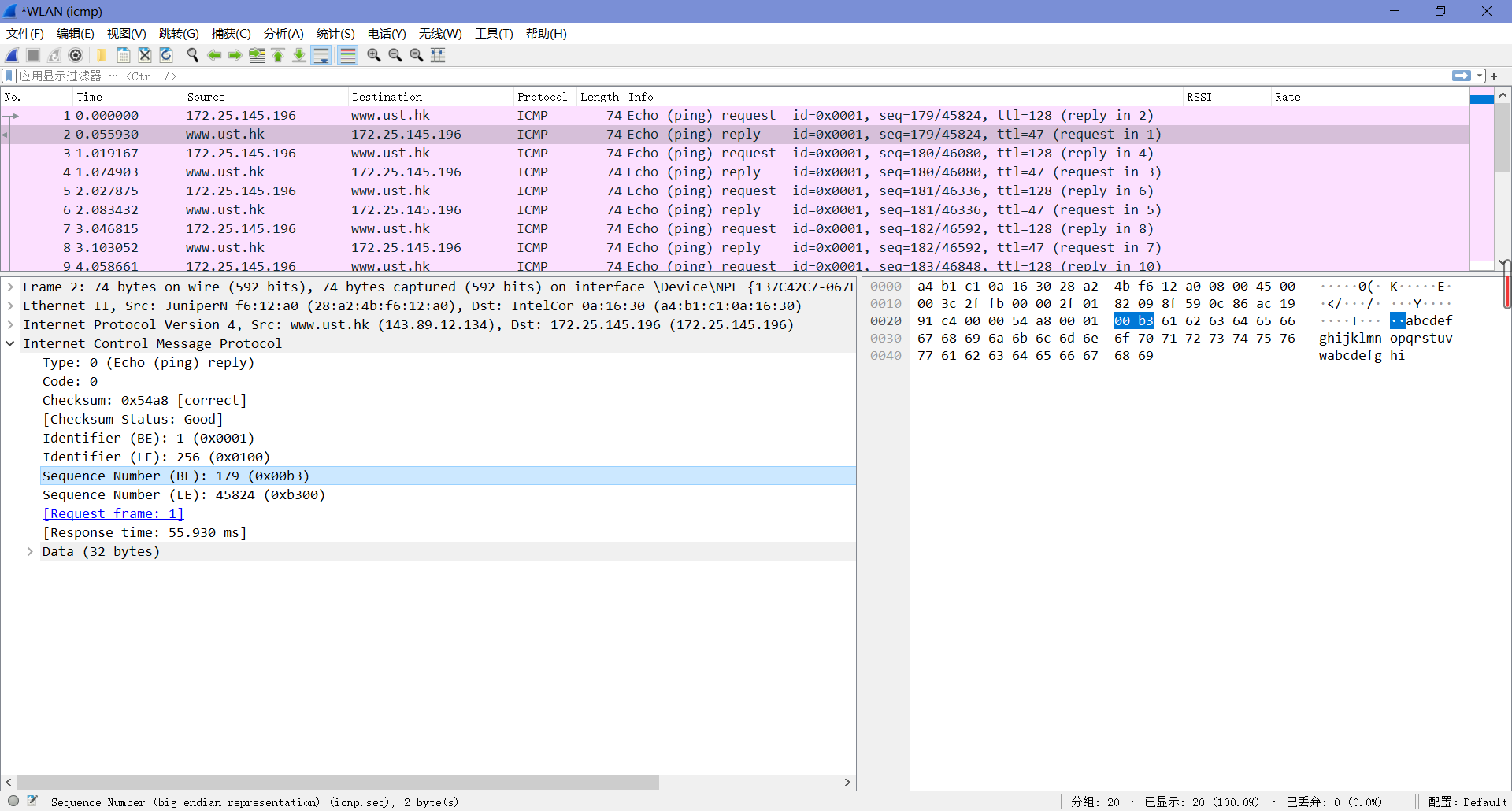
3. Examine one of the ping request packets sent by your host. What are the ICMP type and code numbers? What other fields does this ICMP packet have? How many bytes are the checksum, sequence number and identifier fields?
由下图可知,Type值为8,Code值为0。这个ICMP包中还有校验和、标识符和序列号,各自占了两字节。
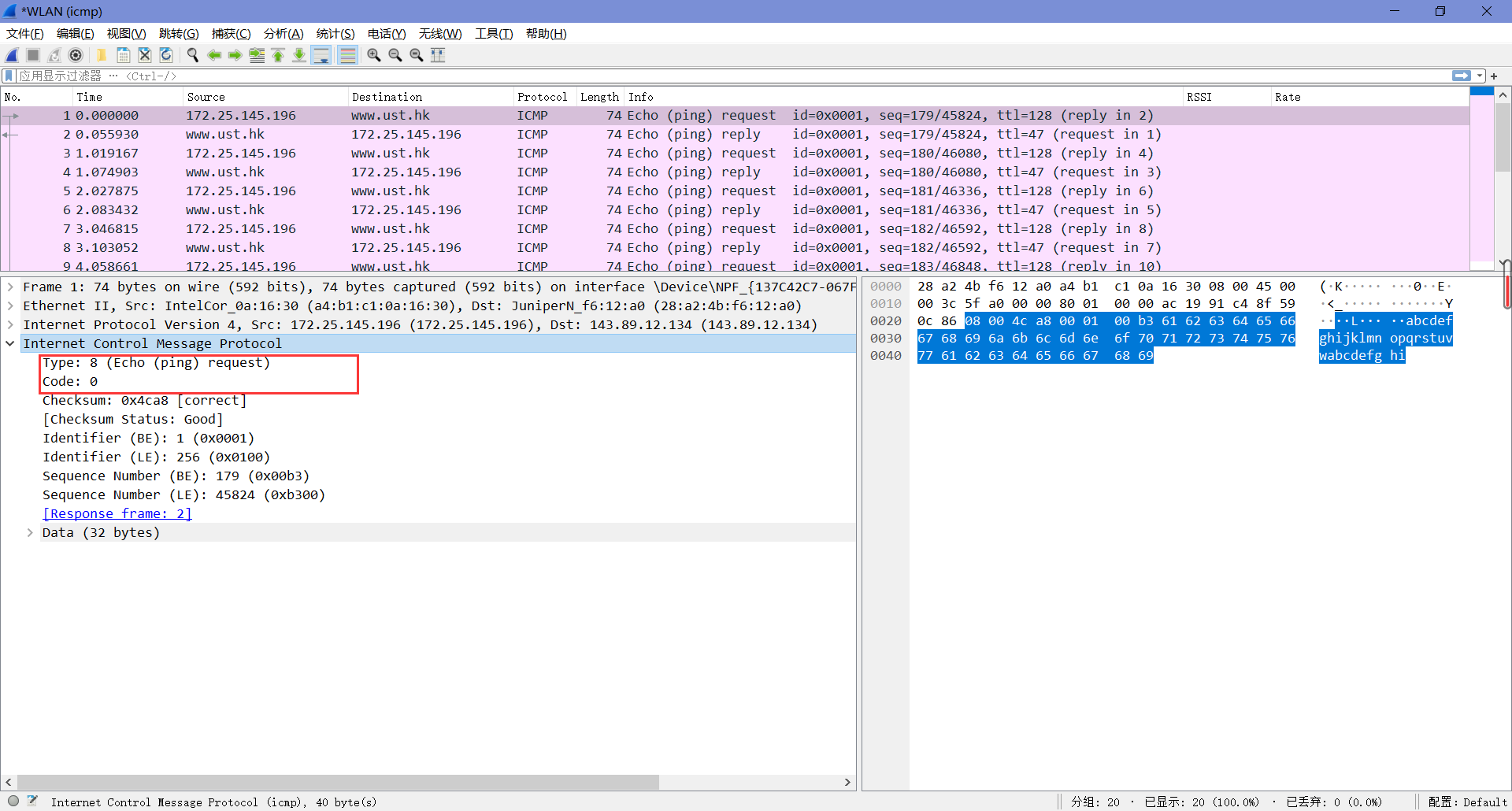
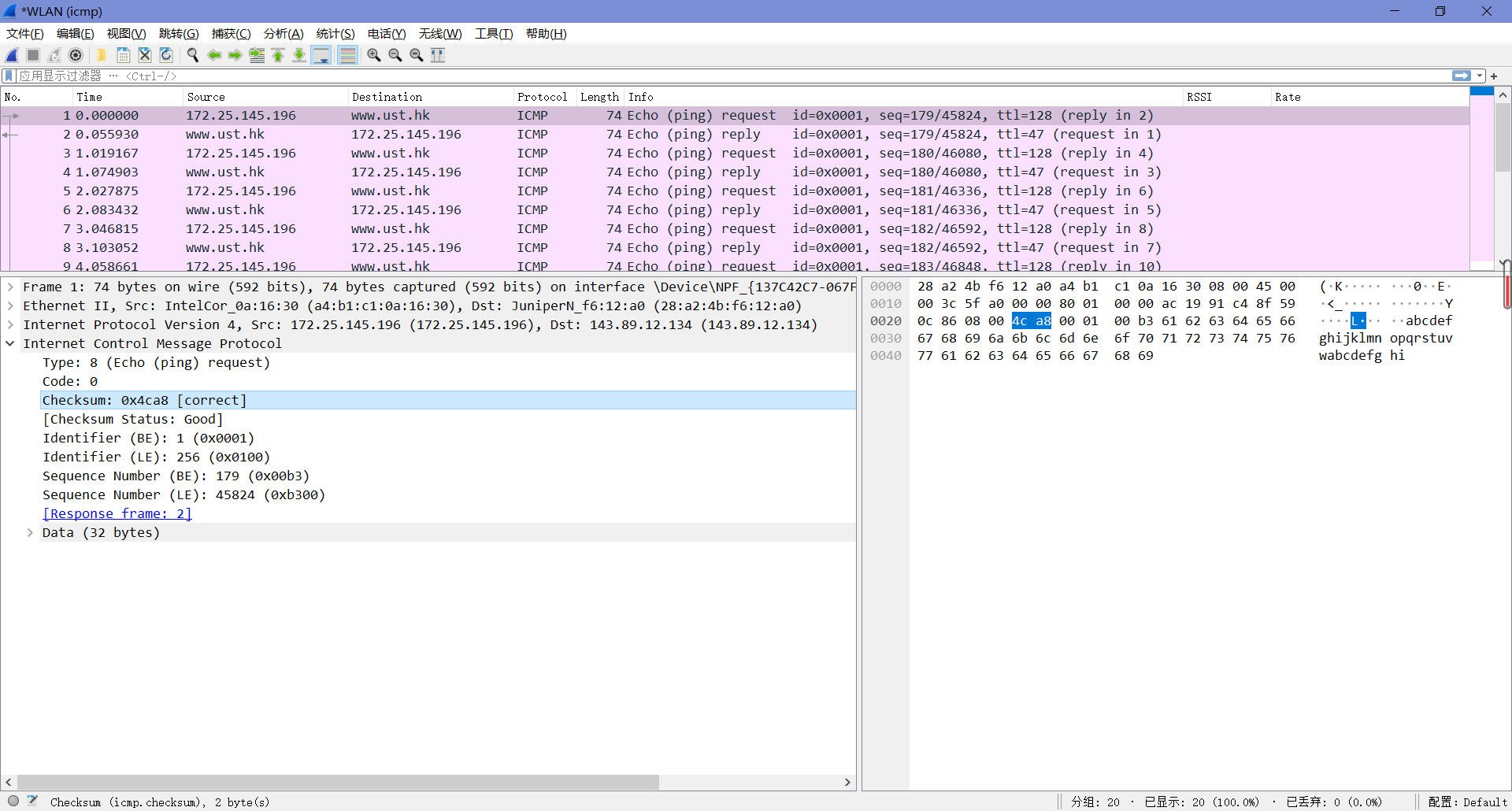
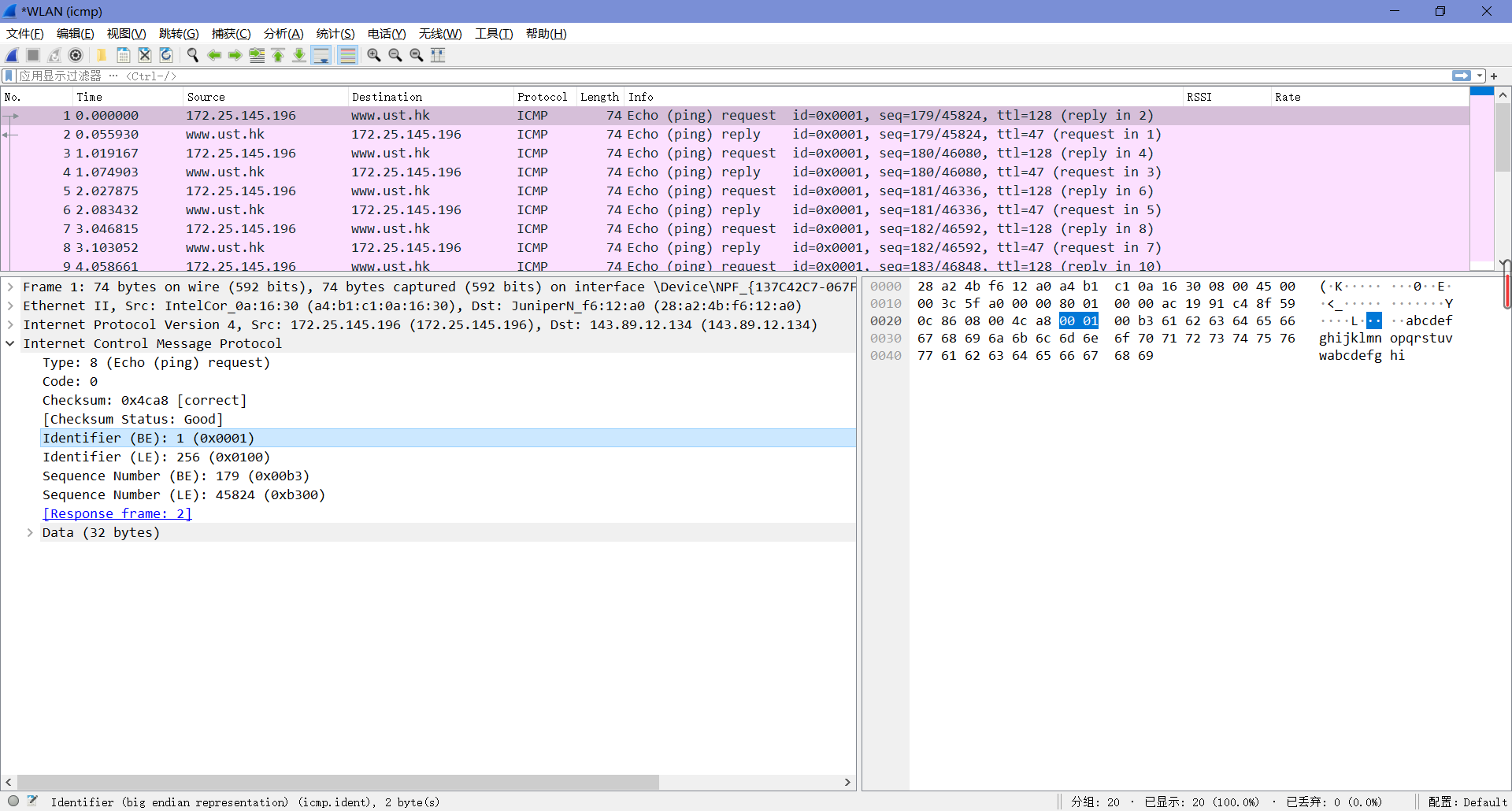
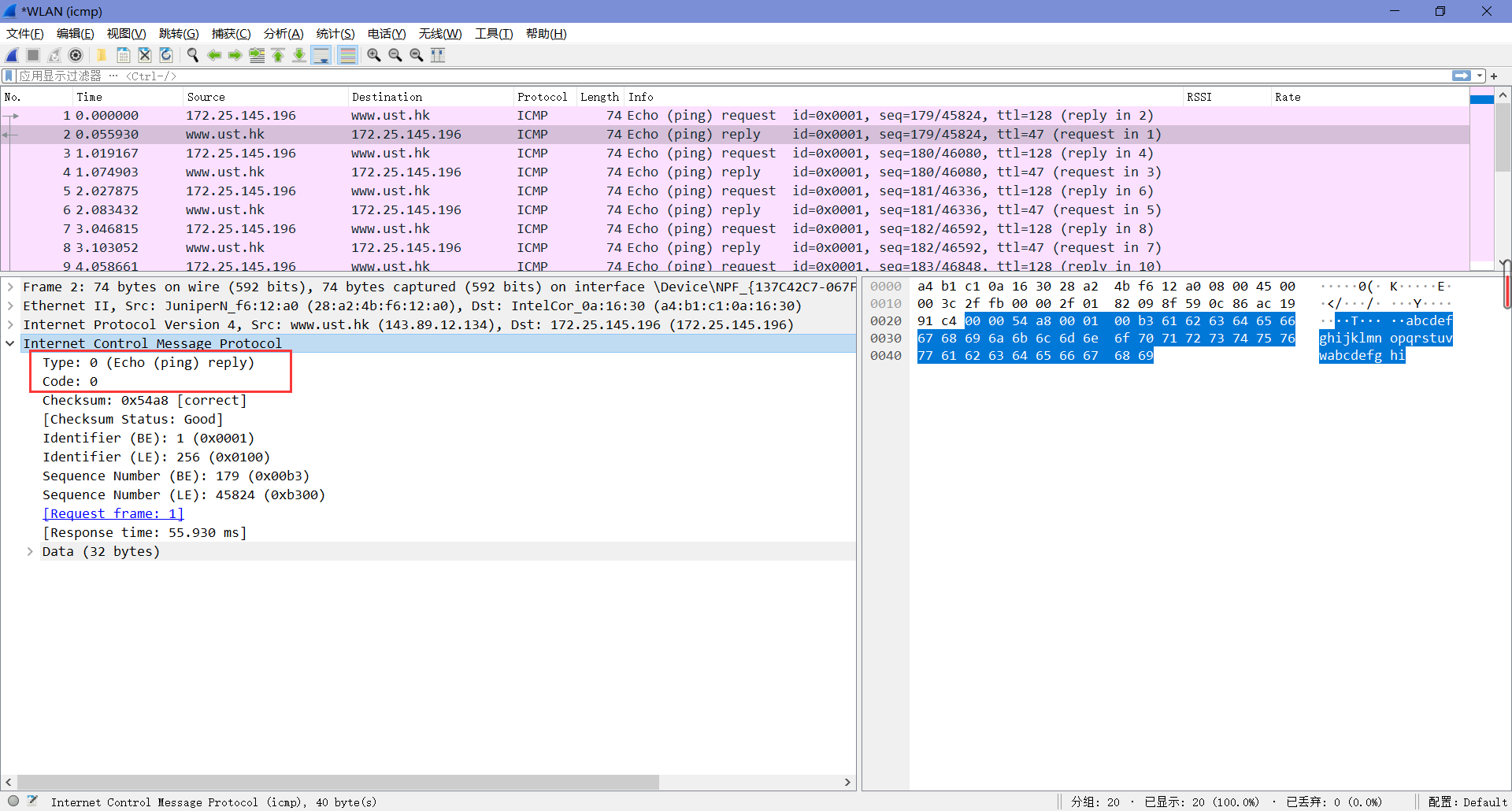
4. Examine the corresponding ping reply packet. What are the ICMP type and code numbers? What other fields does this ICMP packet have? How many bytes are the checksum, sequence number and identifier fields?
由下图可知,Type值为0,Code值为0。这个ICMP包中还有校验和、标识符、序列号和响应时间,各自占了两字节。
Step 2: ICMP and Traceroute
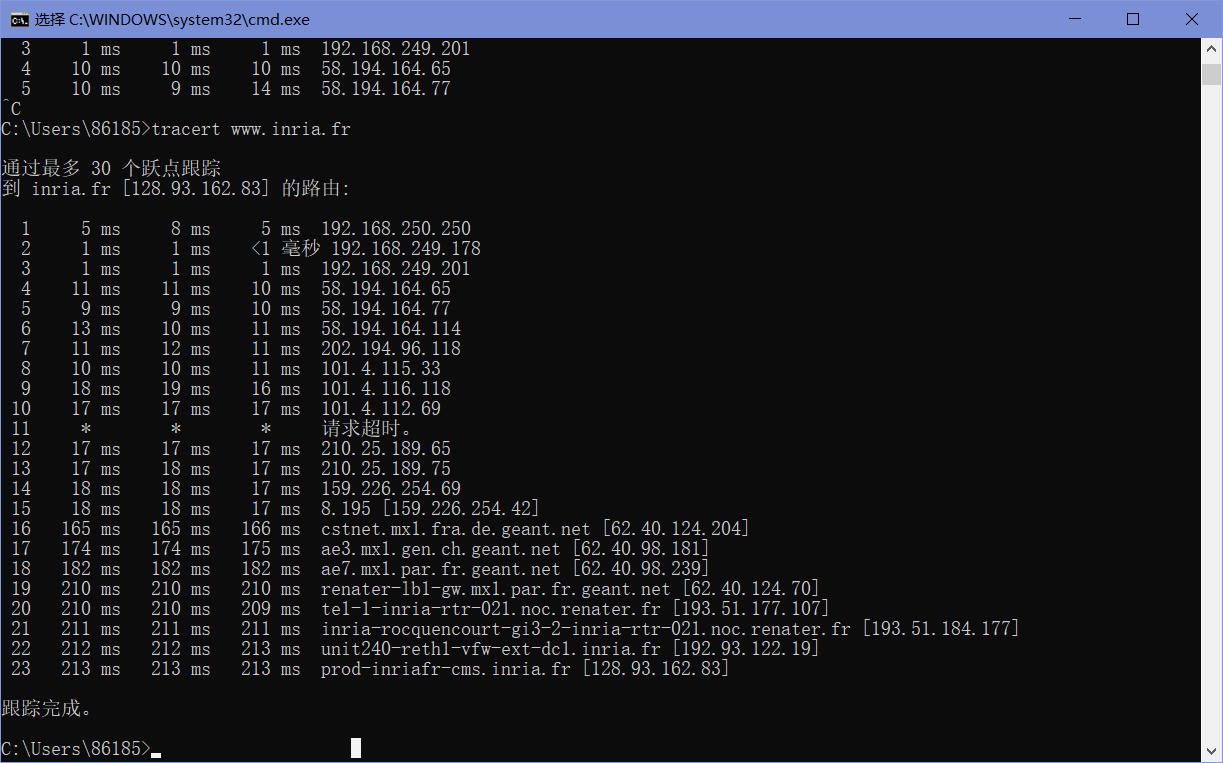
使用Wireshark开始抓包(使用icmp过滤器),然后在命令行中输入”tracert www.inria.fr”,待程序运行结束后停止抓包。
得到如下结果:
5. What is the IP address of your host? What is the IP address of the target destination host?
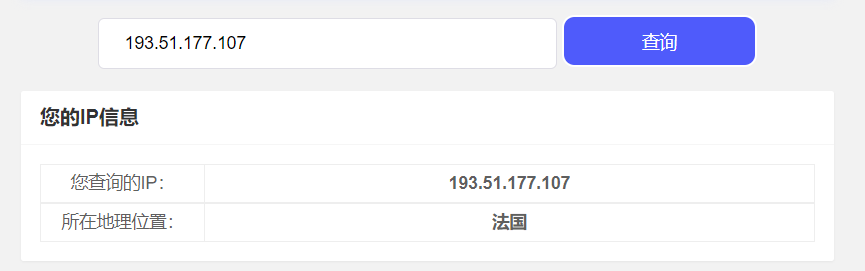
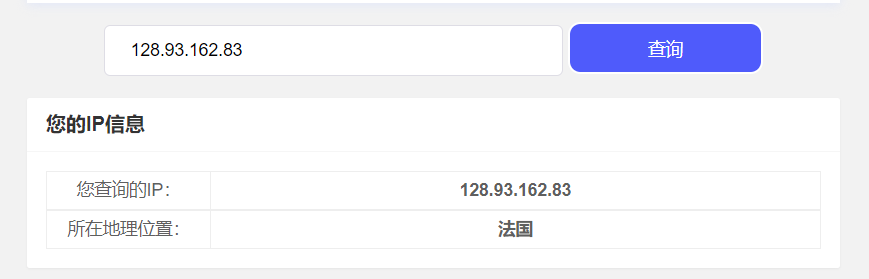
由下图可知,本机IP为172.25.145.196,目标主机IP为128.93.162.83。
6. If ICMP sent UDP packets instead (as in Unix/Linux), would the IP protocol number still be 01 for the probe packets? If not, what would it be?
这里没有抓取到UDP包,查阅资料得知此时数据包的IP协议号不是 01,是17。
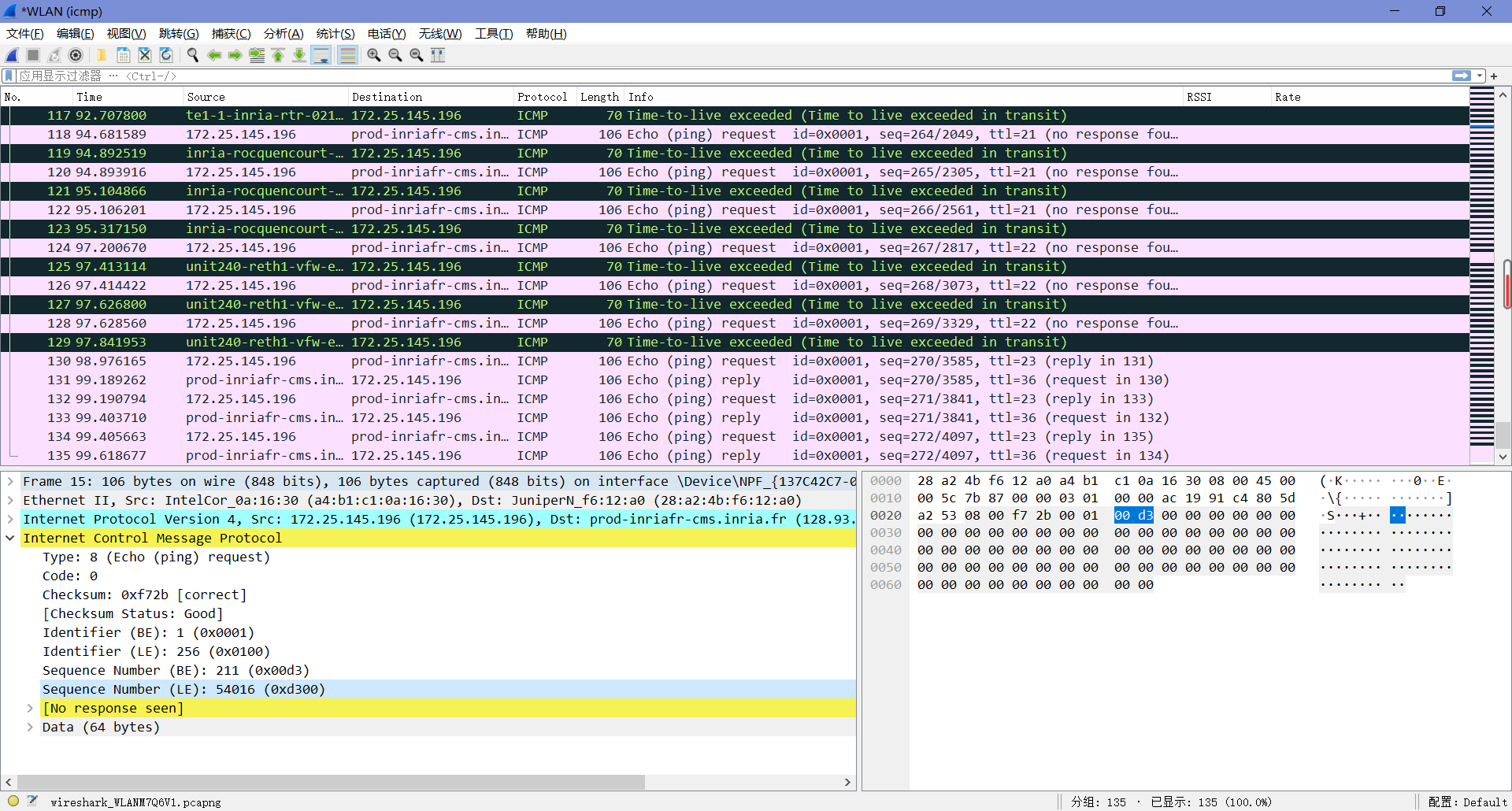
7. Examine the ICMP echo packet in your screenshot. Is this different from the ICMP ping query packets in the first half of this lab? If yes, how so?
不同,前半部分的ping查询数据包中ICMP报文类型为11,表示数据报过期需要丢弃,返回此ICMP报文警告源主机。
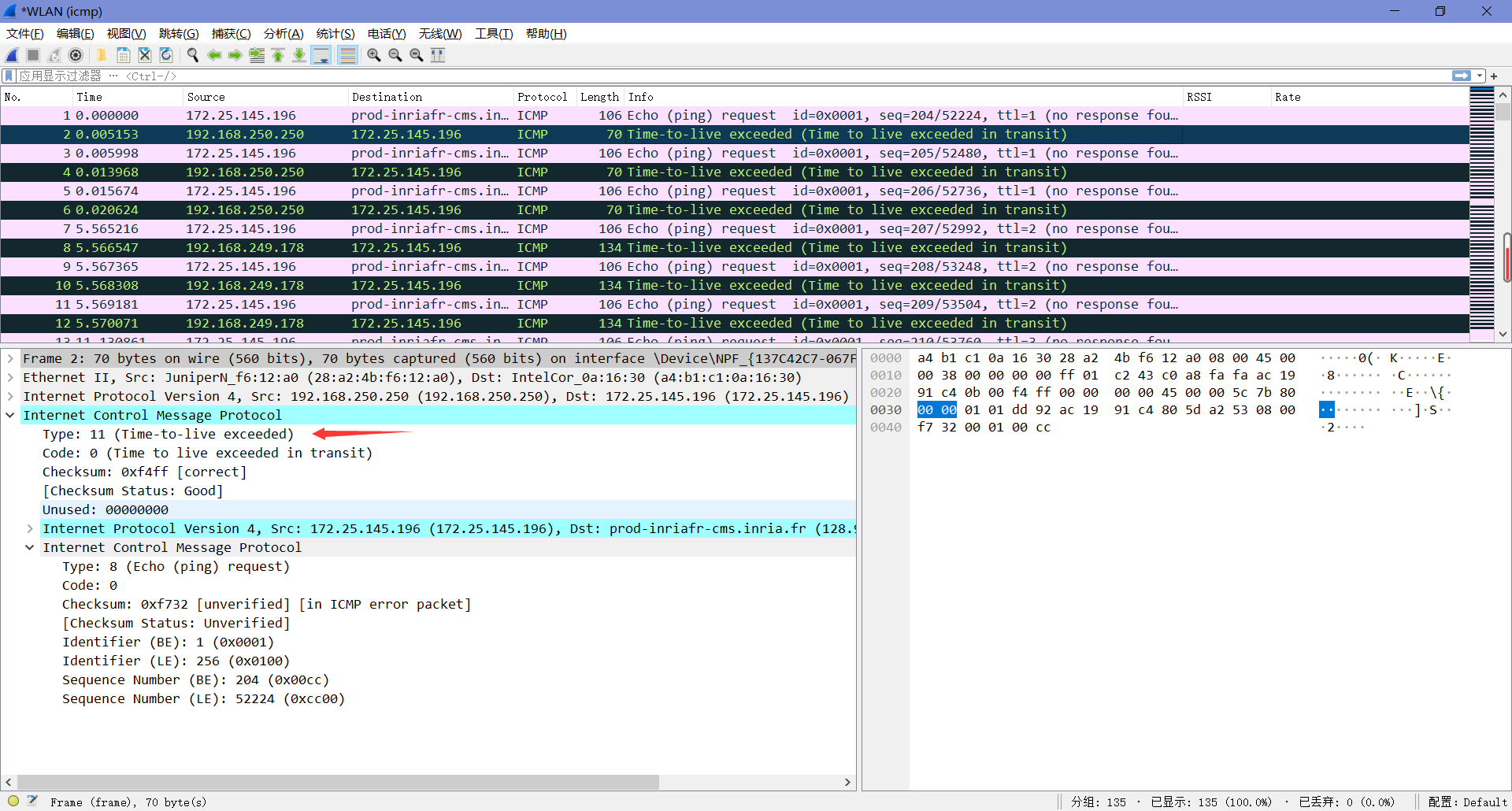
8. Examine the ICMP error packet in your screenshot. It has more fields than the ICMP echo packet. What is included in those fields?
由对比可知,错误的数据包多了请求数据包内容。
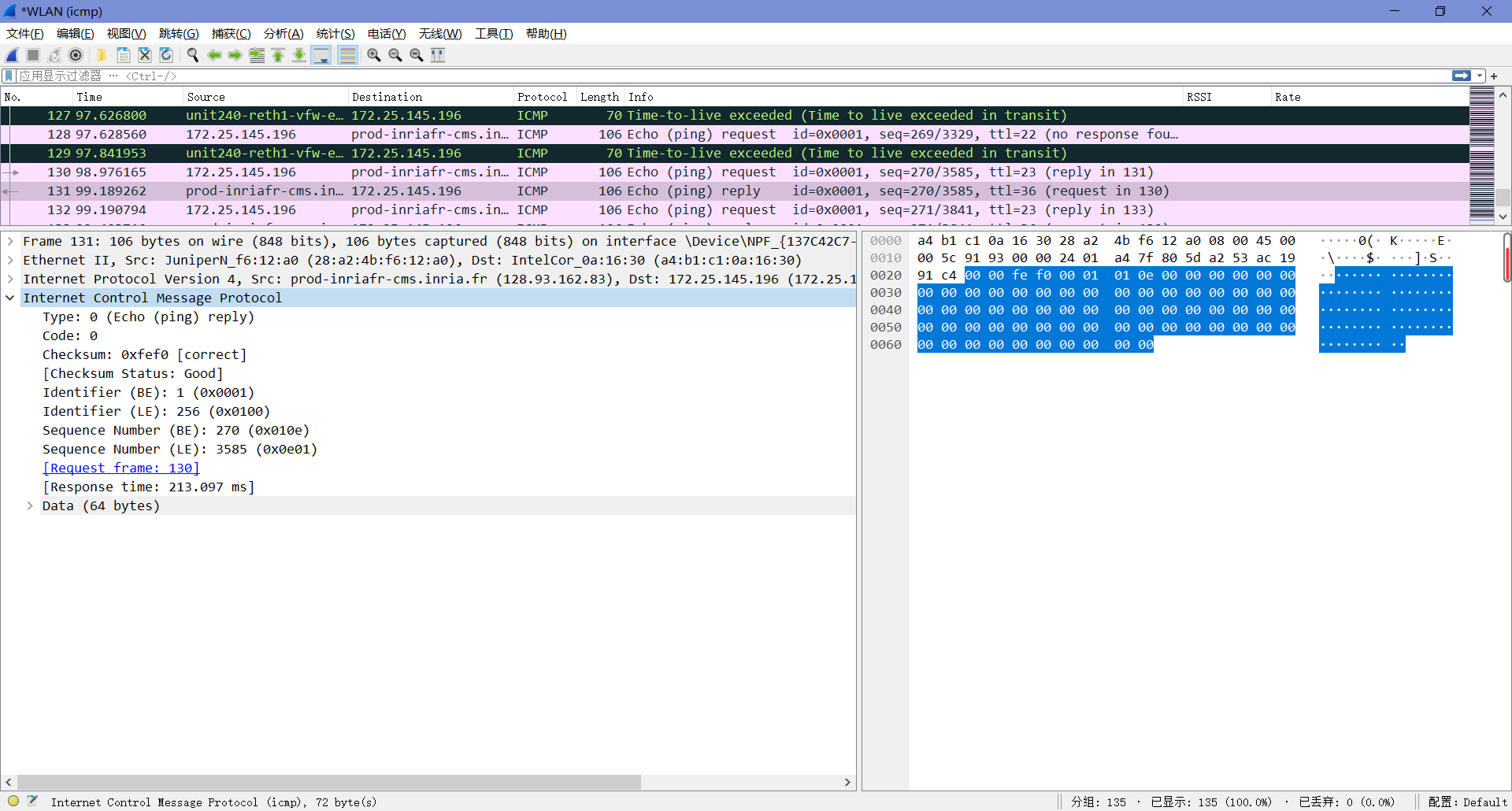
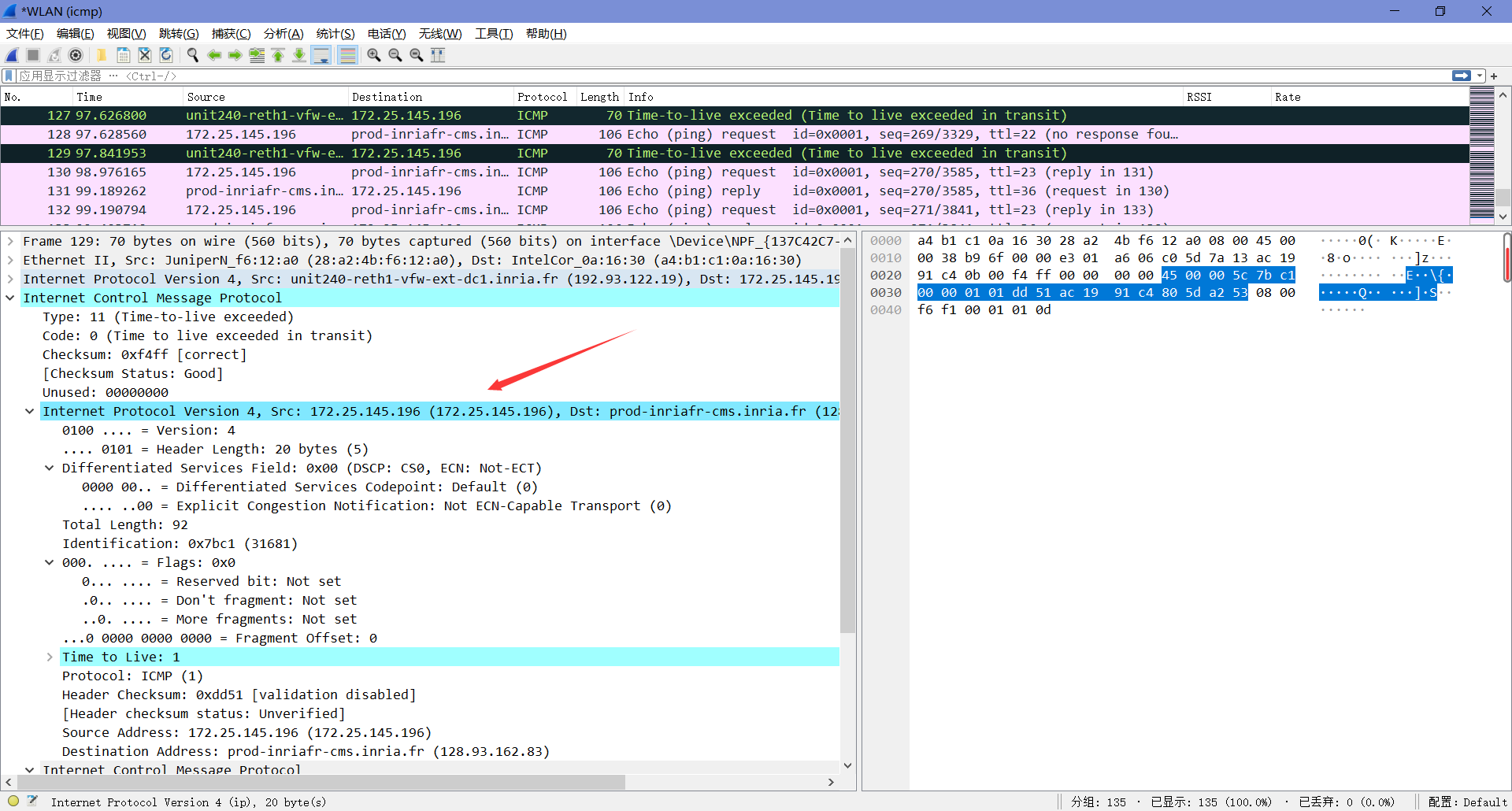
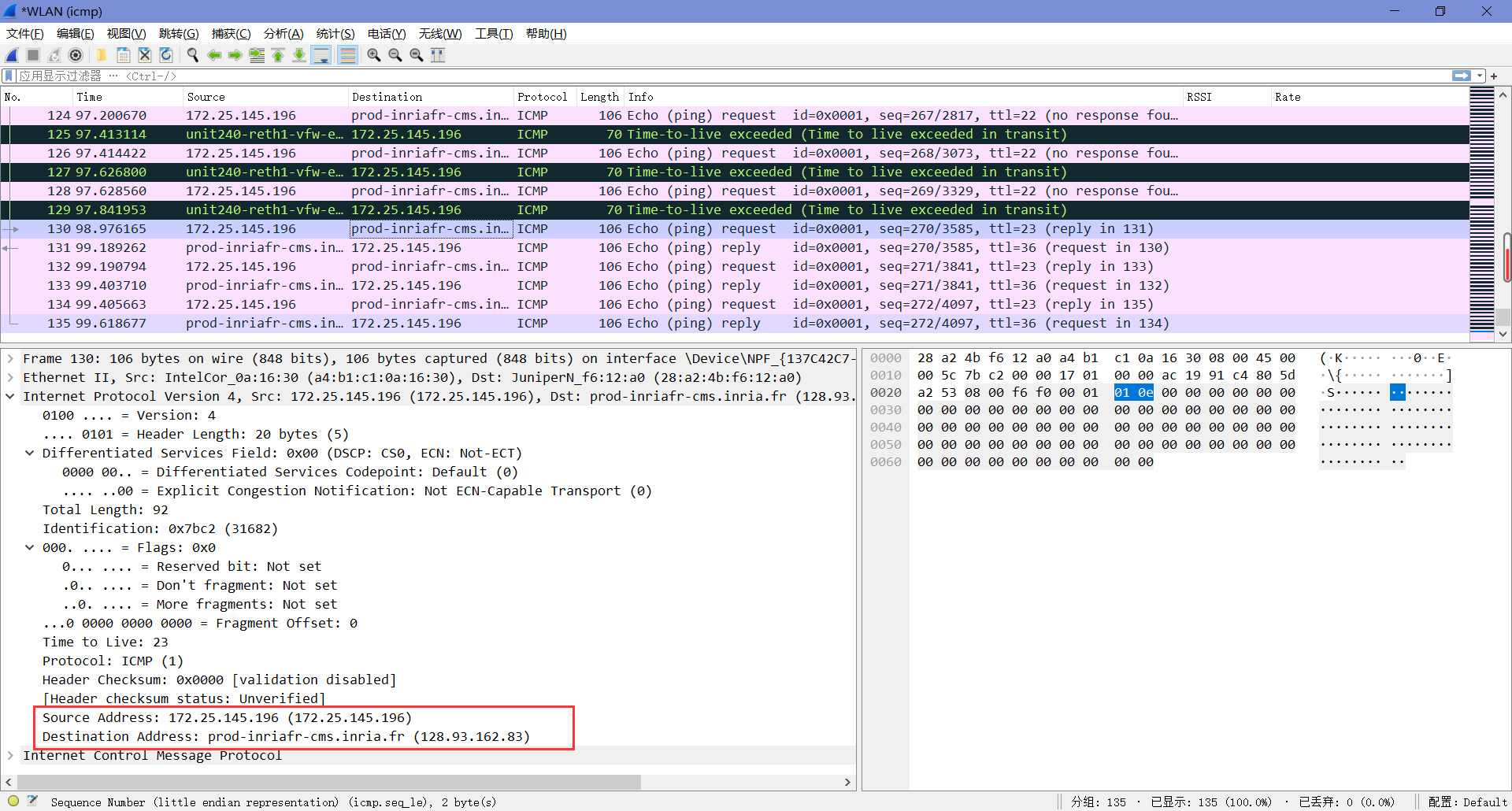
9. Examine the last three ICMP packets received by the source host. How are these packets different from the ICMP error packets? Why are they different?
区别如上题所述,最后三个包正常收到了回复(感觉这里我抓包有问题,搜了搜看了下一些博主做的实验,发现他们有收到我没有收到的icmp包——Type值为3且标注了端点不可达)。
10. Within the tracert measurements, is there a link whose delay is significantly longer than others? Refer to the screenshot in Figure 4, is there a link whose delay is significantly longer than others? On the basis of the router names, can you guess the location of the two routers on the end of this link?
由下图我们可以发现从第16次请求开始,花费时间一下子增长了很多。

使用IP 地址查询查询该IP可以发现其所在地理位置为英国。一直到第19个请求,IP所在的地理位置都为英国。
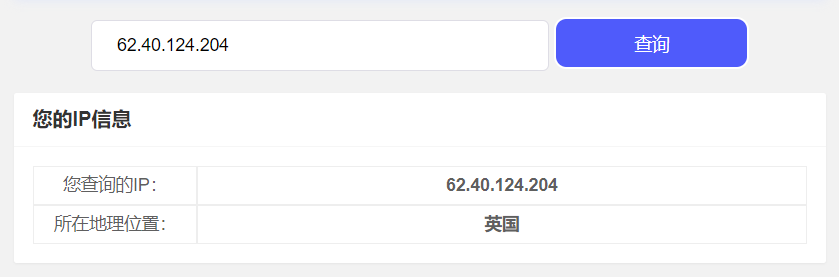
从第20个请求起的后续IP及目标主机IP所在的地理位置均在法国。